Let's Hack an Online Casino - The Consequences of Vibe Coding
Disclaimer
I did disclose all vulnerabilities and they have been fixed. Actually, they completely remade their app (I think because of me). They even segmented their rewards and online casino into two different applications. This was probably a move to improve security after I disclosed the bugs. Anyway, I'd like to express the amount of difficulty it was to get in touch with someone at any of the companies involved. It was terrible...
Intro
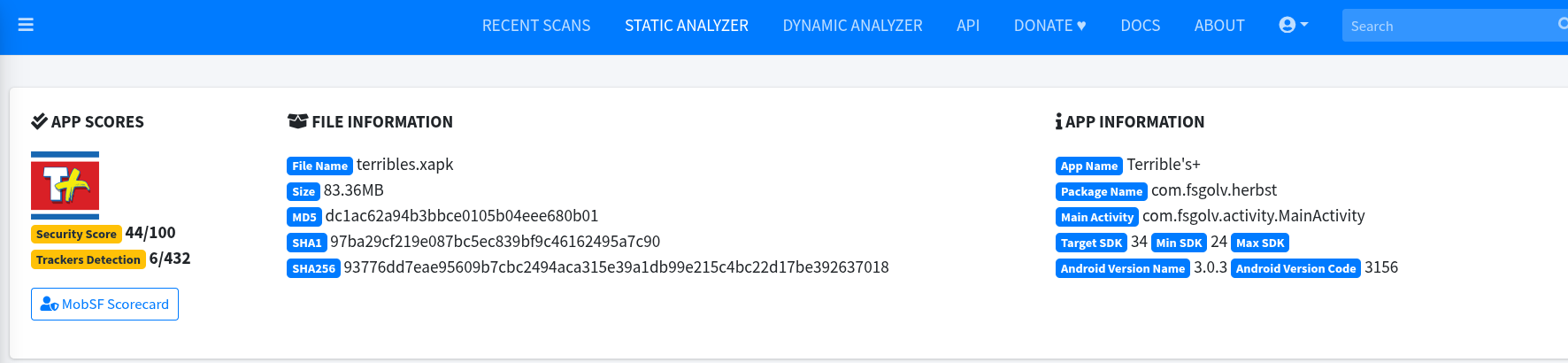
This started as a simple code review of a popular application by the casino/gas station company Terrible's. Their application is loved by many as it unlocks the ability to get free drinks when you fill up your tank. We all need gas, why not get free items with it? Well, the problem is this app like many today hire less real developers and supplement with the use of AI agents. We all know where that leads... So, let's dive right into the fumble of a multiple billion dollar oil/casino company's devops and as to why they decided to outsource their app's development to AI. Additionally, how this may lead to the downfall of other casinos in Las Vegas...
The Beginning
I've been using this app to get free items because we all want free items, right? One day I was told of a policy change that limited the amount of free items which obviously was unfortunate. Because of this my curiosity told to look at the app and I decided to reverse engineer it.
How exactly does the app work? Like any hacker I'm interested in the inner workings of the things I interact with on a daily basis. I fire up the "hacktop" and get ready to sit through some vomits java code. Now, when I want to mess with an app my process generally remains the same:
- Download the apk(s) from https://apkpure.com onto my computer.
- Use jadx in some form to get java code out of said apk(s).
- Look for anything of interest to me.
Lately I've been using https://github.com/MobSF/Mobile-Security-Framework-MobSF for the clean webapp interface.
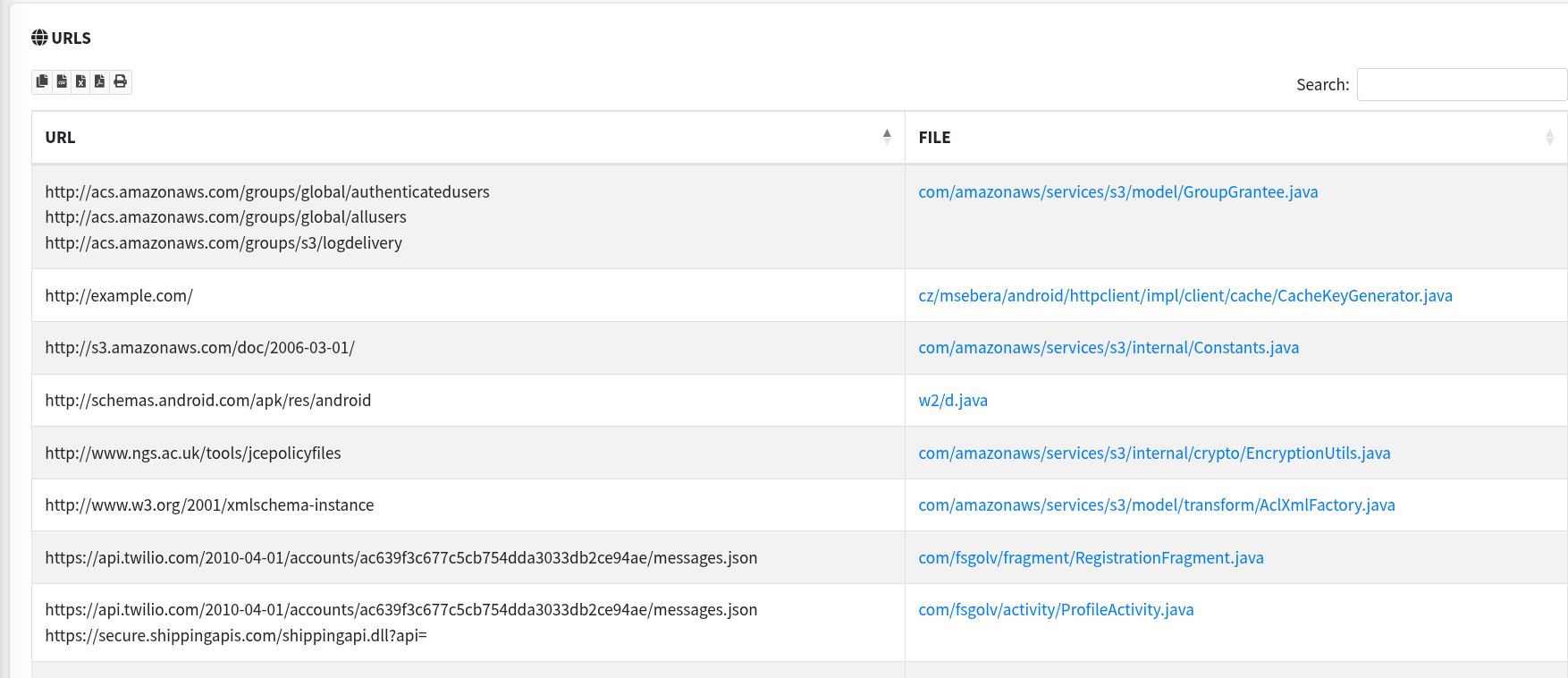
This is great as I can get a lot of information very quickly. It even performs some static code analysis for as well as finds potential secrets being leaked. But that's not how I found this god-awful vulnerability. I found it by looking at the URL's the app hits.
I can see it uses DynamoDB which is Amazon's DBaaS and Twilio for presumably sending sms. Once I clicked on the source code file for registration I almost starting laughing.
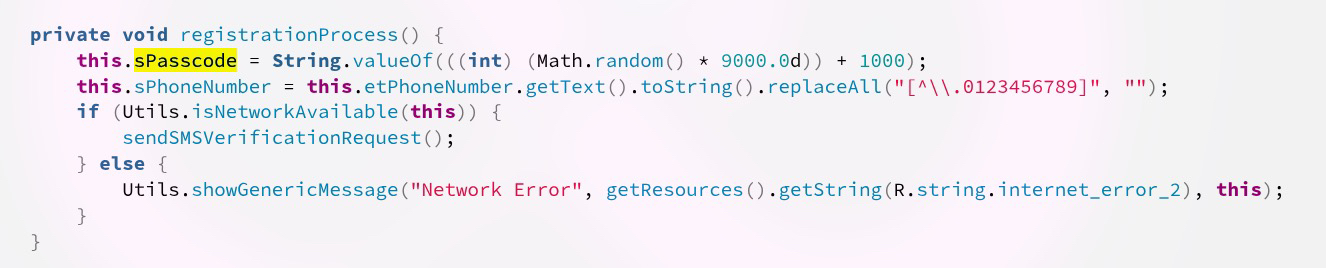
What you're seeing is the registration function that is called during signup which generates an OTP code on the client (don't ever do that). Usually when I see something so idiotic I feel the urge to keep looking harder because if that exists there's more.
Then I realized the same thing was happening for signins... In theory this means I could signin to anyone's account without a password by using a OTP code that I am generating (well the app is generating). This is when we take a break and talk about the importance of NEVER TRUSTING THE CLIENT! With this information a threat actor could get into the account of every single user without a password just generating their own OTP codes and using them. The catch? There really isn't one you just need a number/email. Remember this is a multi-billion dollar casino and their app has in game slots where you can gamble.
Exploitation
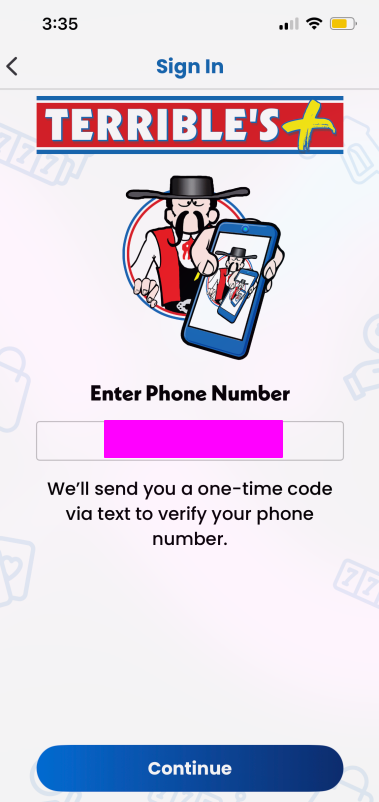
With a bug this bad I decided to go right into exploiting it. There's no way it works I'm thinking. I fire up burpsuite to intercept the requests from my phone and see if it's really sending over the otp to the server.
This is the sign in screen. I started by putting my own number in to see if the OTP code I intercept is the same as the one I get send via sms.
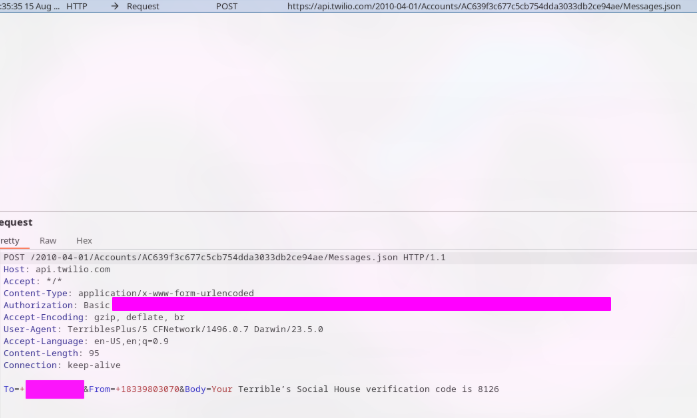
That's the request with an OTP of 8126 let's remember this and let it go through.
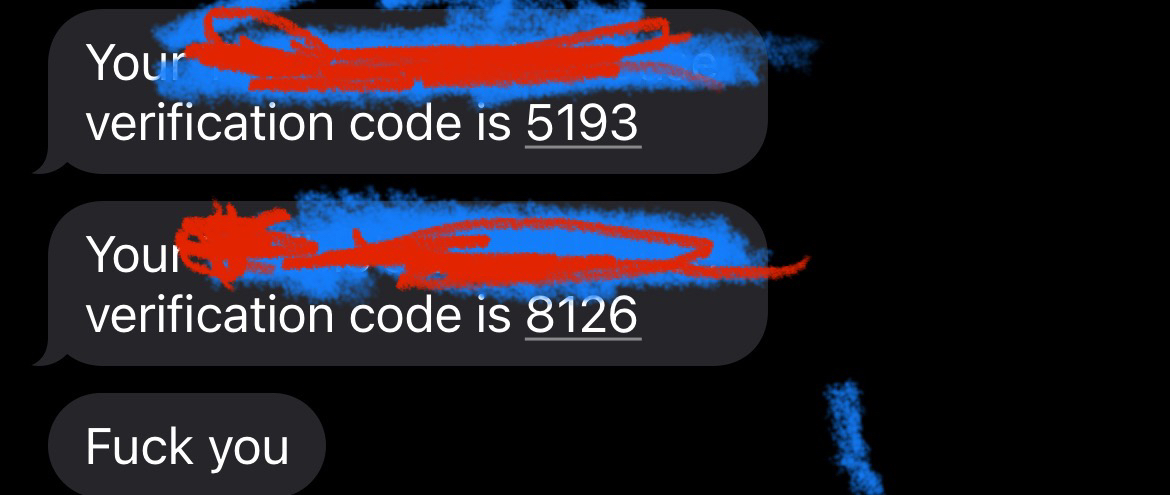
That's the OTP meaning it's possible to capture it. Letting anyone with this knowledge to login to any account. One more thing, did you notice the last message? Yes, that's a custom message because you can edit the request to say anything you want. I tested this further by sending my girl friend a message:
The potential for phishing with this is crazy! This left me wondering about the Authorization header in the request.
Another Problem
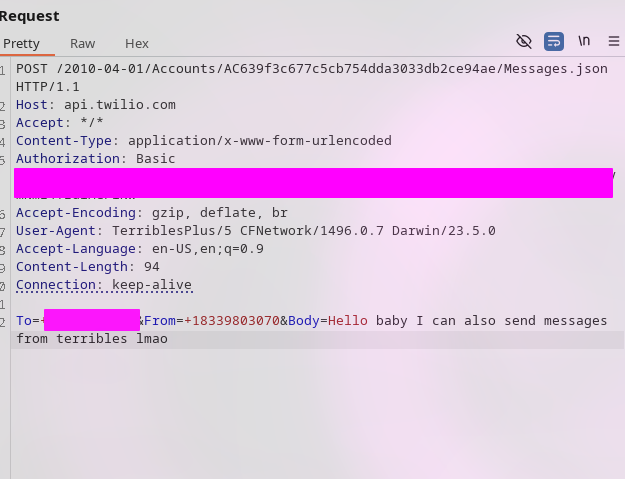
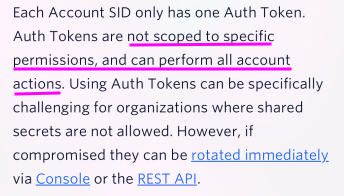
I looked through Twilio's website and found out they're leaking the Auth Token that could let me perform "all account actions". I'm not sure what this entails, let's find out, but first let's make sure everyone understands what I can do:
- I can log into anyone's account.
- I can send anyone messages from Terrible's number.
- I can perform every action on Terrible's Twilio Account.
If I were a threat actor this would be devastating for their company. I won't go into detail on all the terrible terrible things I could do to Terrible's laughs. Just use your imagination and you can think of the possibilities. Fortunately, I'm a good guy and will be responsibly reporting all of this.
Twilio
What is Twilio? Twilio is a cloud communications company which provides programmable communication tools for making and receiving phone calls, sending and receiving text messages, and performing other communication functions using its web service APIs. That's what Wikipedia says about twilio, but to see the functionality I have control over with the leaked auth token I checked their documentation.
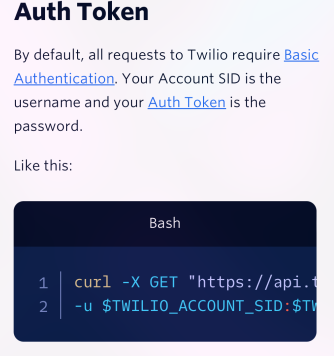
https://www.twilio.com/docs/usage/requests-to-twilio
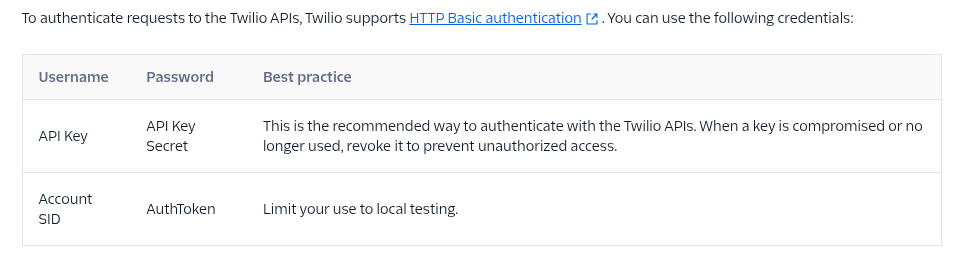
The type of authentication the app is using is the second type. The one that says "Limit your use to local testing". This is where you face-palm while reading this.
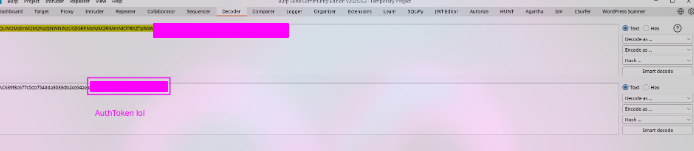
This is definitely the account sid / auth token : separated when I base64 decode it.
It keeps getting worse...
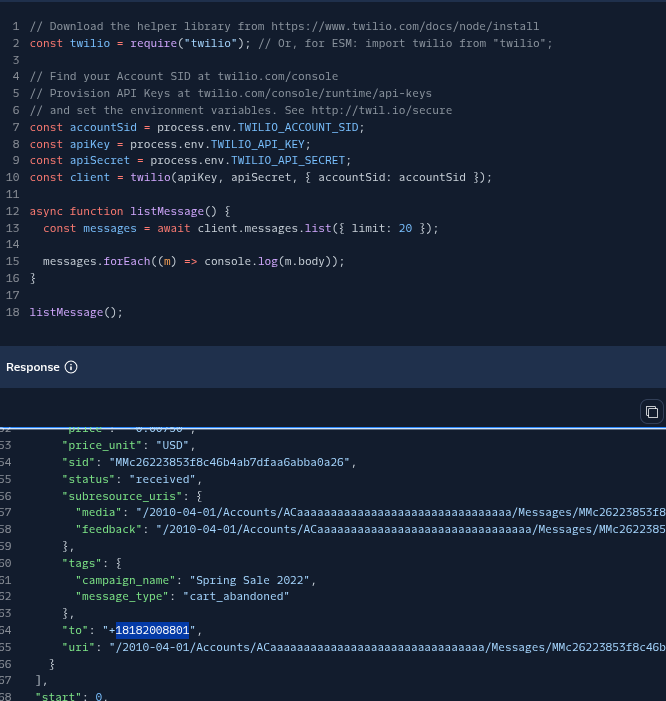
That's a screenshot from the documentation showing how to make a GET request to get all the messages sent. Keep in mind it's showing auth with apikey, but auth token (what I have) can do everything apikey can. If I were a threat actor I now have the first thing I would need to log into every account, or I now know every accounts number to launch a mass phishing campaign (I can still send messages from their number(s)). I could keep going on with the crazy things I could do, like get PII, but you get the point. Speaking about PII... Did you know that Terrible's stores your ID? Well they do. I'm pretty much finished with this, although I'd like to end it off with two messages:
- DON'T TRUST THE CLIENT
- DON'T VIBE CODE
Update
The developers of this app CGT, or "Creative Game Technologies" also made slots apps for other big Las Vegas casinos (4queens, Binions). I don't know if those apps were vulnerable. They most likely were though.